Understanding HalDispatchTable for Windows Vulnerability Research & Exploit Development
Understanding HalDispatchTable for Windows Vulnerability Research & Exploit Development
Hey everyone! Hope you’re all doing well. This is yet another follow up post in the series “Understanding windows internals for vulnerability research & exploit development”. This blog post is on HalDispatchTable, where we will be talking more about its internals instead of just saying “Oh, it’s part of the Hardware Abstraction Layer that deals with hardware stuff” and moving on, we’re going deeper… If you’ve been poking around Windows internals or exploit development, chances are you’ve heard of HAL or even seen HalDispatchTable mentioned in exploits. But how many of you actually understand what HAL really is, what it does under the hood, and why HalDispatchTable was such a popular exploitation primitive back in the day? Well, guess what? That’s exactly what this post is about!”
Well, What the heck is HalDispatchTable?
When it comes to Windows kernel vulnerability research, there are a few structures that have earned a kind of legendary status and one of them is the HalDispatchTable. Sure, it might not be the go-to target in modern exploits anymore (thanks to newer mitigations.. Love hate relationship btw), but understanding what it is and where it fits in the big picture of Windows internals is still super important.
In this post, we’re gonna break it down, not just the HalDispatchTable itself, but also the foundation it sits on: the Hardware Abstraction Layer, or HAL. More specifically, we’ll be looking at hal.dll and what it actually does behind the scenes.
So, According to ChatGPT “The Hardware Abstraction Layer (HAL) in Windows is a core architectural component designed to abstract hardware-specific details from the rest of the operating system. It provides a uniform interface for higher layers of the Windows kernel to interact with hardware without needing to worry about the specifics of the underlying platform.”
LOL, If you didn’t get it, basically the HAL serves as a compatibility layer between the kernel and the raw hardware. Without the HAL, the Windows kernel would need to include conditional logic or separate binaries for different chipsets, I/O buses, interrupt controllers, and multiprocessor configurations. By abstracting these details into a discrete, pluggable layer, the HAL allows Windows to be far more modular and portable..
From a design perspective, the HAL is responsible for critical low-level tasks such as Configuring and routing hardware interrupts, Handling memory-mapped and I/O port access etc etc.. These stuffs make the HAL a critical part of system initialization and runtime behavior. FYI, It allows the same Windows kernel binary (e.g., ntoskrnl.exe ) to work across a wide variety of hardware environments simply by loading an appropriate HAL implementation.
OK, but HOW??
Well, The HAL is implemented through a kernel-mode binary named hal.dll, which is loaded during system boot. Despite the .dll extension, hal.dll is not a user-mode DLL. Instead, it is a privileged, memory-resident module that runs in ring 0 alongside the kernel and other core components. So, During the Windows boot process, the bootloader (e.g., bootmgr or winload.exe) detects the underlying hardware platform and selects the appropriate version of hal.dll. When I was exploring about this, It seems like historically, there were multiple HAL variants (e.g., halacpi.dll, halapic.dll) optimized for different configurations, but I guess this has been streamlined in newer versions of Windows since I haven’t seen any of these DLLs (If you have seen it, accept that you are in your 40s!)
Once loaded, hal.dll is mapped into the kernel address space and initialized through entry points such as HalInitSystem (You can go through its code from ReactOS here). These initialization routines set up critical subsystems, including the Advanced Programmable Interrupt Controller (APIC) or legacy PIC, System clock and timer mechanisms, Low-level power management interfaces, High-resolution performance counters etc..
Additionally, hal.dll exports a number of low-level routines and interfaces used by the kernel and device drivers. These include HalQuerySystemInformation(), HalSetSystemInformation() etc.. These routines are not accessed directly via calls to hal.dll as one might do with user-mode DLLs. Instead, they are wired into kernel logic via function pointers, either exposed explicitly or encapsulated within structures like the HalDispatchTable (More on this in next section). We are making progress guys!!! Stay with me!
What is the HalDispatchTable?
The HalDispatchTable is a global kernel structure that contains pointers to several of these HAL routines. It's essentially a table of function pointers residing in non-paged kernel memory, meaning its contents are always resident and accessible by privileged code. This table serves as an internal dispatch mechanism for certain system-level operations. For instance, if a syscall like NtQueryIntervalProfile needs to interact with the hardware timer, the kernel might route the call through an entry in the HalDispatchTable, which in turn points to HalQuerySystemInformation() inside hal.dll.
Taking reference from ReactOS doc, its structure would be like this,
typedef struct {
ULONG Version;
pHalQuerySystemInformation HalQuerySystemInformation;
pHalSetSystemInformation HalSetSystemInformation;
pHalQueryBusSlots HalQueryBusSlots;
ULONG Spare1;
pHalExamineMBR HalExamineMBR;
#if 1 /* Not present in WDK 7600 */
pHalIoAssignDriveLetters HalIoAssignDriveLetters;
#endif
pHalIoReadPartitionTable HalIoReadPartitionTable;
pHalIoSetPartitionInformation HalIoSetPartitionInformation;
pHalIoWritePartitionTable HalIoWritePartitionTable;
pHalHandlerForBus HalReferenceHandlerForBus;
pHalReferenceBusHandler HalReferenceBusHandler;
pHalReferenceBusHandler HalDereferenceBusHandler;
pHalInitPnpDriver HalInitPnpDriver;
pHalInitPowerManagement HalInitPowerManagement;
pHalGetDmaAdapter HalGetDmaAdapter;
pHalGetInterruptTranslator HalGetInterruptTranslator;
pHalStartMirroring HalStartMirroring;
pHalEndMirroring HalEndMirroring;
pHalMirrorPhysicalMemory HalMirrorPhysicalMemory;
pHalEndOfBoot HalEndOfBoot;
pHalMirrorVerify HalMirrorVerify;
pHalGetAcpiTable HalGetCachedAcpiTable;
pHalSetPciErrorHandlerCallback HalSetPciErrorHandlerCallback;
#if defined(_IA64_)
pHalGetErrorCapList HalGetErrorCapList;
pHalInjectError HalInjectError;
#endif
} HAL_DISPATCH, *PHAL_DISPATCH;
Accessing these entries involves dereferencing kernel pointers something that’s only possible from ring 0 code.. From a stackoverflow page, I also found that in earlier versions of Windows (such as XP and Server 2003), these entries were both writable and indirectly reachable from user mode via system calls. No wonder why they got beaten-up very bad LOL because if someone could achieve an arbitrary write primitive, they could overwrite one of these entries with a pointer to their shellcode and trigger it via a syscall.
HalDispatchTable: How It’s Located, Mapped, and Accessed by the Kernel
Understanding how the HalDispatchTable is actually used by the kernel requires stepping through what happens at runtime and. not just the structure’s definition in the symbol files, but how it’s resolved and dereferenced by core system routines. Once the kernel and hal.dll are mapped into memory, a pointer to the HalDispatchTable structure is typically placed at a well-known location in earlier versions, or discovered through symbols or scanning in newer ones. For example, in Windows XP, it could be found at 0xFFD03000. But with Kernel Address Space Layout Randomization (KASLR), these locations are no longer fixed and must be determined dynamically at runtime.
Now, you may ask how is it actually used?
So, Let’s take NtQueryIntervalProfile as an example. When a user-mode process calls this API, the syscall eventually transitions into kernel mode via ntdll.dll. Once inside ring 0, the kernel’s system service dispatcher uses a service table (like SSDT) to route execution to a native kernel handler, which may look like this (simplified):
If you disassemble the NtQueryIntervalProfile() in WinDbg, you will see that a function called KeQueryIntervalProfile() is called in this function:
uf nt!NtQueryIntervalProfile:
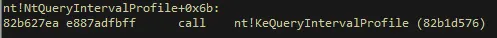
If we disassemble the KeQueryIntervalProfile(), you can see the HalDispatchTable actually gets called by this function, via a pointer!
uf nt!KeQueryIntervalProfile:
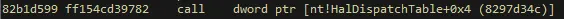
Essentially, the address at HalDispatchTable + 0x4, is passed via KeQueryIntervalProfile(). If we can overwrite that pointer with a pointer to our user mode shellcode, natural execution will eventually execute our shellcode, when NtQueryIntervalProfile() (which calls KeQueryIntervalProfile()) is called!
//Reference :http://undocumented.ntinternals.net/index.html?page=UserMode%2FUndocumented%20Functions%2FNT%20Objects%2FProfile%2FNtQueryIntervalProfile.html
NTSTATUS NtQueryIntervalProfile(
KPROFILE_SOURCE ProfileSource,
PULONG Interval
) {
if (!Interval)
return STATUS_INVALID_PARAMETER;
*Interval = ((HAL_QUERY_SYSTEM_INFORMATION)(HalDispatchTable[0]))(ProfileSource);
return STATUS_SUCCESS;
}
Here, HalDispatchTable[0] points to HalQuerySystemInformation, a function implemented within hal.dll. The kernel does not directly call hal!HalQuerySystemInformation; instead, it dereferences a pointer stored in HalDispatchTable. This level of indirection makes it easy to replace HAL routines with alternate implementations. This indirect dispatching mechanism is deeply baked into the Windows architecture. Multiple core NT routines rely on dispatch tables, not just for HAL, but also for power management, ACPI handling, and more.
Memory Layout and Access.. Freaking Finally!
As I said earlier, On systems without SMEP or modern mitigation strategies, HalDispatchTable could be both writable and executable. This meant if you had any form of write-what-where primitive say, from a buffer overflow or double-fetch vulnerability.. you could overwrite an entry with a user-mode address (such as shellcode in virtual memory), and then trigger it via a system call that referenced that entry.
Internally, the Windows kernel does not perform deep validation of internal function pointers for performance reasons. It expects these structures to remain trustworthy — this is part of the implicit trust model of kernel-mode code. It’s worth emphasizing that while HalDispatchTable is accessible only from kernel mode, the triggers that eventually reach into it (via system calls) originate from user mode!

HOLD ON!! In modern Windows versions, direct access to HalDispatchTable is far more restricted. It’s now protected by:
- Kernel Patch Protection (PatchGuard) — Tampering with this structure results in a bug check.
- SMEP (Supervisor Mode Execution Prevention) — Prevents kernel from executing user-mode pages.
- KASLR (Kernel Address Space Layout Randomization) — Obscures address of the table.
As I always mention in my posts, there may be many other primitives beyond this. I’m far from calling myself a vulnerability researcher , I still have a lot to learn and explore. These are just some of the primitives I came across while reading other blogs, and I’m always grateful to the authors who take the time to document the root cause analysis of the bugs they discover.
That’s all for now! Hope you guys find this post interesting and useful. Follow me on LinkedIn, Medium, X.
PEACE!
REFERENCES:
[Windows Kernel-Mode HAL Library - Windows drivers
Windows kernel-mode HAL library
learn.microsoft.com](https://learn.microsoft.com/en-us/windows-hardware/drivers/kernel/windows-kernel-mode-hal-library?source=post_page-----417568ec60c2---------------------------------------)
[What is a Hardware Abstraction Layer and How Does it Work?
Learn what hardware abstraction layer (HAL) is, the function of HAL in computing systems, and how it affects…
www.lenovo.com](https://www.lenovo.com/in/en/glossary/hardware-abstraction-layer/?orgRef=https%253A%252F%252Fwww.google.com%252F&srsltid=AfmBOormazAgONlkteNtPg8cYoUlbbs7SGnrrEDOx910wv0jkYzNo3uV&source=post_page-----417568ec60c2---------------------------------------)